Introduction
Since the historic launch of the Soviet Sputnik 1, satellites have become a vital component of Critical Infrastructure (CI), transforming how we communicate, gather data, and understand the world around us. These artificial objects orbiting our planet have been deeply integrated into the public and private domains, for the use of earth observation, communication, navigation, and even national security. Therefore, it comes to no surprise that satellites are a prime target for malicious actors such as insiders, hactivists, terrorist groups, cyber criminals and nation-states.
A recent example of this phenomenon is the October 7th, 2023 terrorist attack when the Harakat al-Muqawama al-Islamiya, otherwise known as the Hamas Islamic Resistance Movement carried out a jamming attack on the Israeli Global Positioning System (GPS) signals, surpassing the it’s technological capabilities [1]. Military organizations heavily utilize GPS for Positioning, Navigation, and Timing (PNT), enhancing precision in military operations and facilitating efficient transportation and communication. Up to this point, the system’s inadequate resilience to operate or recover from the distruption, has resulted in fatality of over 1,300 lives among both Israelis and Palestinians [2]. While this is just one example, concerning security, it’s not uncommon to encounter satellite exploitation incidents due to their significance, which can result in damage to both tangible and intangible assets.
The following blog article introduces satellite systems security to cybersecurity students in a manner that remains coherent, even when discussing complex concepts like orbital mechanics, space engineering, and ethical hacking. By the end of the blog article, cybersecurity students will have a brief idea of the current state of satellite systems security in research and problems associated with the current trends from a technological, legal and ethical point of view.
From Inception to Present
In 1957, the launch of Sputnik 1 marked a pivotal moment as the first satellite to be launched into space. Its primary and only mission was to transmit signals to Soviet ground stations [3]. Unsuprisingly due to the cold war, this achievement intensified the competition between the polar opposite, United States and the Soviet Union. As noted by James Pavur, a security researcher at The University of Oxford, three years later, in 1962, a pivotal moment in the history of satellite security took place during a U.S. congressional hearing [1]. This act, signed by President John F. Kennedy, deliberated the inclusion of private enterprises in space activities under the Communications Satellite Act 1962, otherwise known as “ComSec”, expanding commercial communication satellite operations in the United States. From a historical standpoint, this event is a direct consequence of the contemporary space industry, often denoted as ‘New Space.’
As of today, unlike the United Kingdom and the European Union, the United States does not classify satellites as part of Critical Infrastructure [5] even noting that in 2023, more than 8500 active satellites were recoded orbiting our planet, supporting a market value of around $383 billion [1]. Satellite related activities currently contribute £370 billion to the United Kingdom (UK) economy, which is around 17.7% of the UK’s GDP [1]. Satellites, mainly utilized for communication and categorized as Low-Earth Orbit (LEO), comprise 80% of the satellites, underpinning a wide range of services. This includes delivering over 100 Terabytes/Second of global internet capacity and broadcasting media content to an audience of more than 100 million customers [2]. To gain an indepth understanding of the contemporary challenges from a technical standpoint, it is imperative to firstly grasp the fundamental structures at play.
Space Systems: Structure
Satellite systems, can be broadly divided into three main focuses.
-
- Satellites, orbiting at a defined distance from Earth. Satellites can be defined numerous ways, however, for the purpose of this blog article, adopting the definition from the Oxford Dictionary is the most suitable, which states that satellites can be described as ‘an artificial object placed in orbit around the Earth or another planet for the purpose of collecting information or facilitating communication‘. [6] It is therefore noted that scientifcly utilised interplanetary probes are out of the scope of this specific blog article.
- Ground Stations, typically situate at a specific locations on Earth and part of the wider communication terrestrial systems. Since there is no suitable definition for ground stations, they will be defined as ‘facilities within the ground segment used for simultaneous communication, data sensing, and transmission to satellites’.
- Radio Frequency (RF), commonly referred to as the Uplink/Downlink, situated between the ground station and the satellite. In essence, it is the signal or frequency that connects the ground station and satellite together [refer to fig. 1].
Although one may be easier to exploit than the other, it’s concerning that all three components lack comprehensive industry research and security sector solutions. This is particularly worrisome considering that even leading entities in the United States, such as The National Aeronautics and Space Administration (NASA) in the public domain and Space Exploration Technologies Corporation (SpaceX) in the commercial domain, have not significantly fortified this niche. To establish a theoretical, and technical foundation for the underlying complex mechanisms of these components, the following subsections cover some of the cybersecurity, physics and engineering concepts associated with satellites.
Satellite and Ground Station Systems
Modern space systems are generally complex and multifaceted and may require decades of expertise in the field to understand how they interconnect, however ground stations may be closely represented by Figure 1. Many ground stations utilise widely available hardware such as Software Defined Radios (SDRs) which are used to communicate with flyby satellites. AES (Advanced Encryption Standard), RSA (Rivest-Shamir-Adleman), Diffie-Hellman Key Exchange for encryption.
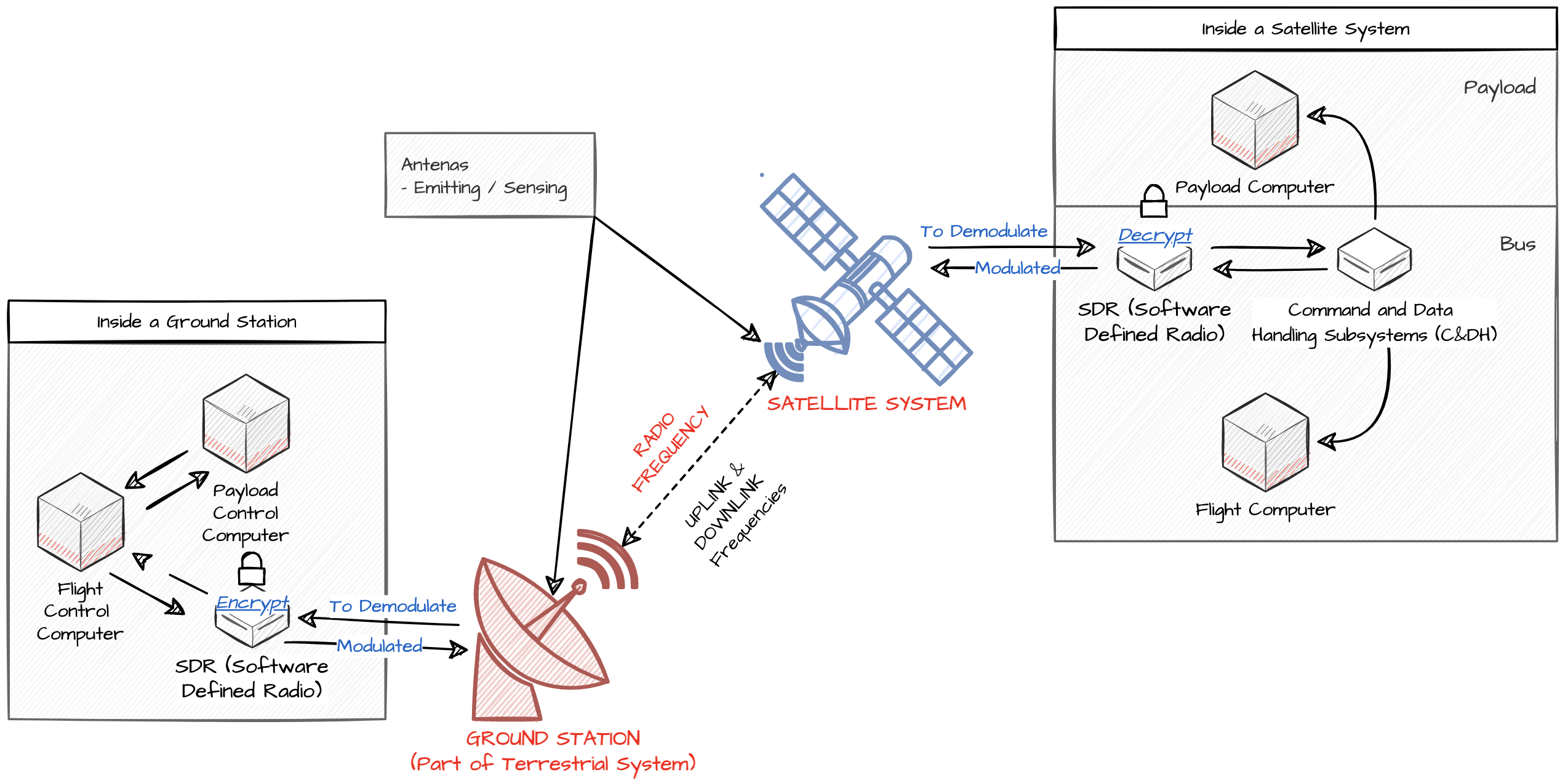
One of the challenges associated with the existing satellite systems is the high saturation of bespoke systems, including the use of Commercial Off-The-Shell Components (COTS) [4]. With this in mind, it is, therefore, it is hard to standardize the layout and the architecture of satellites. Regardless of this issue, the following diagram provides a general overview of the most common utilised hardware used within to demonstrate the generally required knowledge of satellite systems for cybersecurity experts.
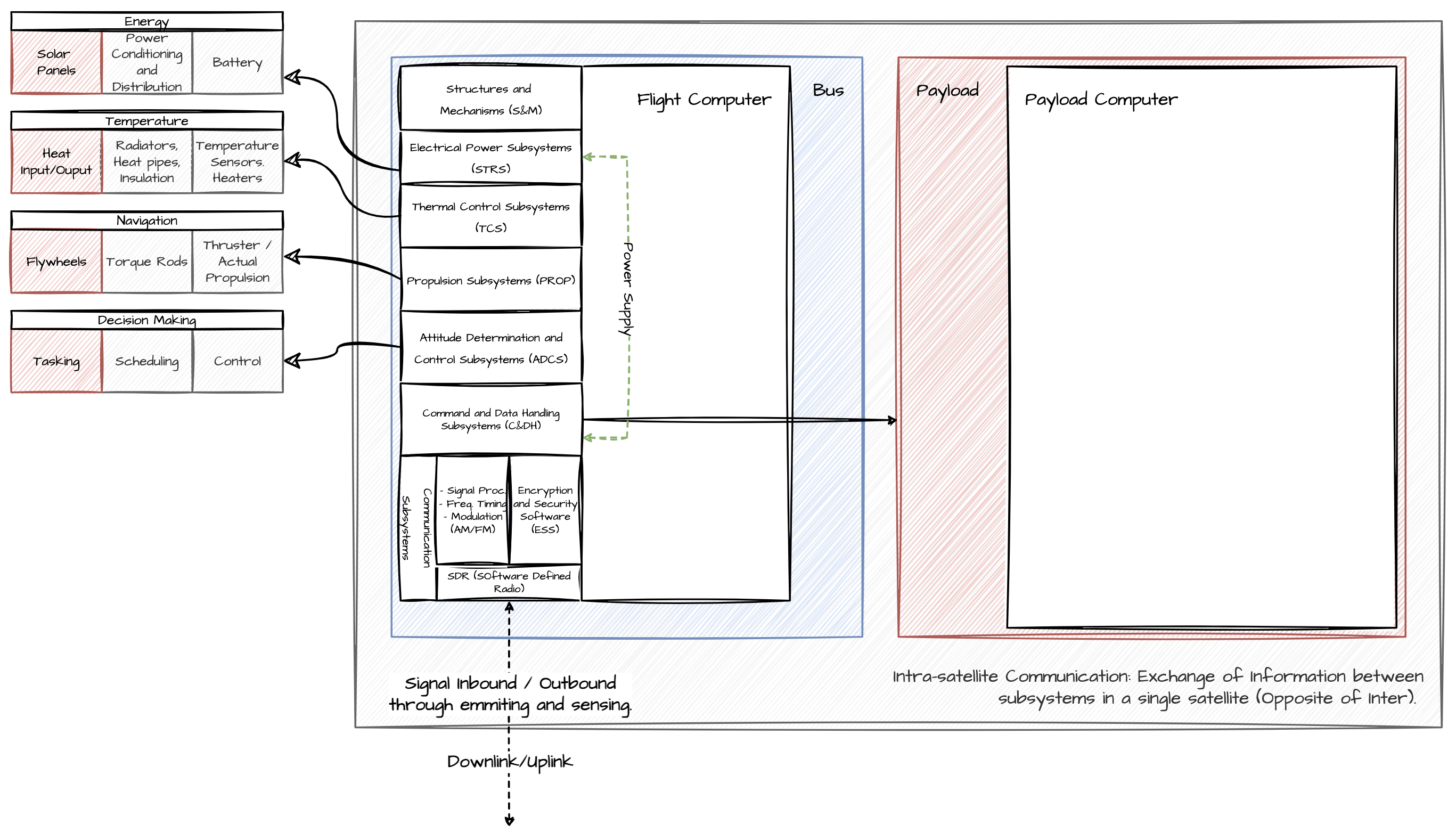
Which components are heavily software relant? And what can be done about them for example SpaceOS? “Position + Time + Attitude” …
Enviromental Challenges
Radiation. Corrosion appears on materials. Ultra Violet energy of radiation wave is higher than the organic chemical bond energy that keeps the material together. As a result, there is decomposition of materials. Gravity. Temperature
Technological Challenges
Energy Consumption. Computer Resource. Collisions
Space Systems: Types
Geosynchronous (GEO) satellites are positioned approximately 35,786 kilometres above the planet’s surface. This specific orbital distance allows these satellites to complete one orbit in precisely 24 hours, keeping them in a fixed position relative to Earth. This synchronization is possible because their orbital velocity (speed) matches Earth’s rotation.
A minimum number of three GEO satellites is required to cover the Earth’s surface effectively. They are primarily utilized for various applications, including telecommunications, broadcasting, remote sensing, and navigation.
Medium Earth Orbit (MEO)
Period: 2 to 24 hours. Navigation, Communication – (Global Positioning System (GPS) + BeiDou are intercompatible). 6 Satellites needed to make a network around orbit.
Low Earth Orbit (LEO)
200 / 2000km – Need a lot of LEOs to make a network around the orbit. Period: 1.5h to 2h. Most used orbit, need for constellations. Need to be replaced quite often. Relatively small coverage with complex ground network.
Satellite Networks
-
- Iridium Constellation: Lots of satellite connected at different position with a similar distance between them.
- GPS Constellation (MEO): Many but not lot of satellites connected optimised for transfer time and coverage.
Current Day Problems
Before delving into the intricacies of current day problems, it is important to acknowledge the issue from a broader perspective. Satellite system security is an inherently multifaceted field of cybersecurity, demanding professionals to possess high-level expertise encompassing both engineering and physics. This implies that proffesionals already established in the industry, who wish to get involved in this specialized domain, may need to undergo additional training and academic studies in the fields of engineering and physics. From a cybersecurity perspective, the confidentiality, integrity, and availability (CIA) Triad stands as a foundational concept. However, it is worth noting that the CIA Triad does not inherently safeguard the cyber-physical systems such as satellites.
In simpler terms, Operational Security (OT) security is distinct from traditional Information Technology (IT) security, which primarily concerns data protection. Professor Christopher Hankin, the Proffesor of Computing at Imperial College London, delved into this topic from a different yet closely related perspective during one of his initial lectures to the 2023/24 MSc Security and Resilience program students.
“Operational Technology security is concerned with the protection of the systems processes against unathorised access. In contrast to Information Technology security, which is concerned with protecting data against unathorised access.”
– Professor Christopher Hankin, Professor of Computing
Technological
The first technological security challenge associated with the existing satellite systems, is the high saturation of bespoke systems, including Commercial Off-The-Shell Components (COTS) [4]. With this in mind, it is hard to standardize the layout and architecture of satellites. Systems security experts such as Greggory Falco from John Hopkins, James Pavur and Ivan Martinovich from The University of Oxford have already raised these issues as early as 2021. However, the probem is approached by changing the current technologies as they are. The problem with this approach is that retrofitting solutions are expensive. Considering the future of satellites, especially those categorized as LEO, will likely be involved in smart cities, autonomous vehicles and upcoming advancements such as 6G.
“Retrofitting is inefficient and cost-worthy. Inculcating security and resilience by design however, is a better approach.”
– Proffesor Washington Yotto Ochieng, EBS, FREng, Director of The Institute for Security Science and Technology.
The second technological challenge associated with satellite systems is their vulnerability as single points of failure. In simpler terms, if a nation-state attacker gains access to the ground station, which controls the flight and payload control computer, and proceeds to transmit signals to the satellites, these satellites will inherently trust whatever they receive from the ground station. Alternatively, if the attacker sends a stronger signal to the satellite, effectively eavesdropping on the communication, the satellite will still trust the stronger signal.
A recent example of a buffer overflow vulnerablity which was exploited in a satellite security was the…
Legal
The collision problem. No Ownership in Space.
Ethical
Space derbis and litering in space especially LEO.
Credits and References
[2] https://ora.ox.ac.uk/objects/uuid:11e1b32a-8117-46b1-a0ce-9c485221d112